20 October 2020
By: Jared Naude, Cloud Architect – Synthesis Software Technologies
As companies go to cloud, they must adopt a new operating model to effectively build and run their environment. In this blog post, which is the first part of a two-part series, we will explore a few key aspects of unlocking the cloud operating model and achieving operational excellence during the cloud journey.
In the era of rapid technological change, the cloud is key for future-proofing businesses and maintaining a competitive edge. Businesses that are migrating their applications and infrastructure into the cloud can benefit from the latest technology and move away from their aging on-premises infrastructure, putting them at the forefront of innovation.
The Cloud Journey and Cloud Operating Model
The question facing enterprises today is not should we go to cloud but how do we go to cloud? As Africa’s first AWS Advanced Consulting partner, we know that the journey to the cloud is not always easy. Organizations may experience uneasiness during the journey especially the fear of the unknown and the large number of decisions that they need to make.
It is critical that an operating model is formed as organizations go through this journey. It may be tempting to take existing on-premises procedures and processes into the cloud. However, doing so will lead to failure as the cloud is significantly different from on-premises infrastructure. Some of the main drivers to adopt cloud technology include minimizing operational costs, workforce productivity, cost avoidance, operational resilience, and business agility. By not re-examining the operating model, organizations will not unlock the true benefits of cloud.
Organizations must consider what new techniques and processes can be put in place to help with the provisioning, securing, connecting and management of cloud environments. One of these techniques is the adoption of DevOps in the organization, it enables applications to be delivered faster while ensuring quality control and minimizing operational overhead. To maximize efficiency and to ensure that cloud practices are adopted, organizations need to create a virtual highway for teams to get to the cloud, this includes onboarding material, clear governance processes and technical enablement which may consist of both appropriate tooling and training.
Provisioning – Reproducible Infrastructure as Code
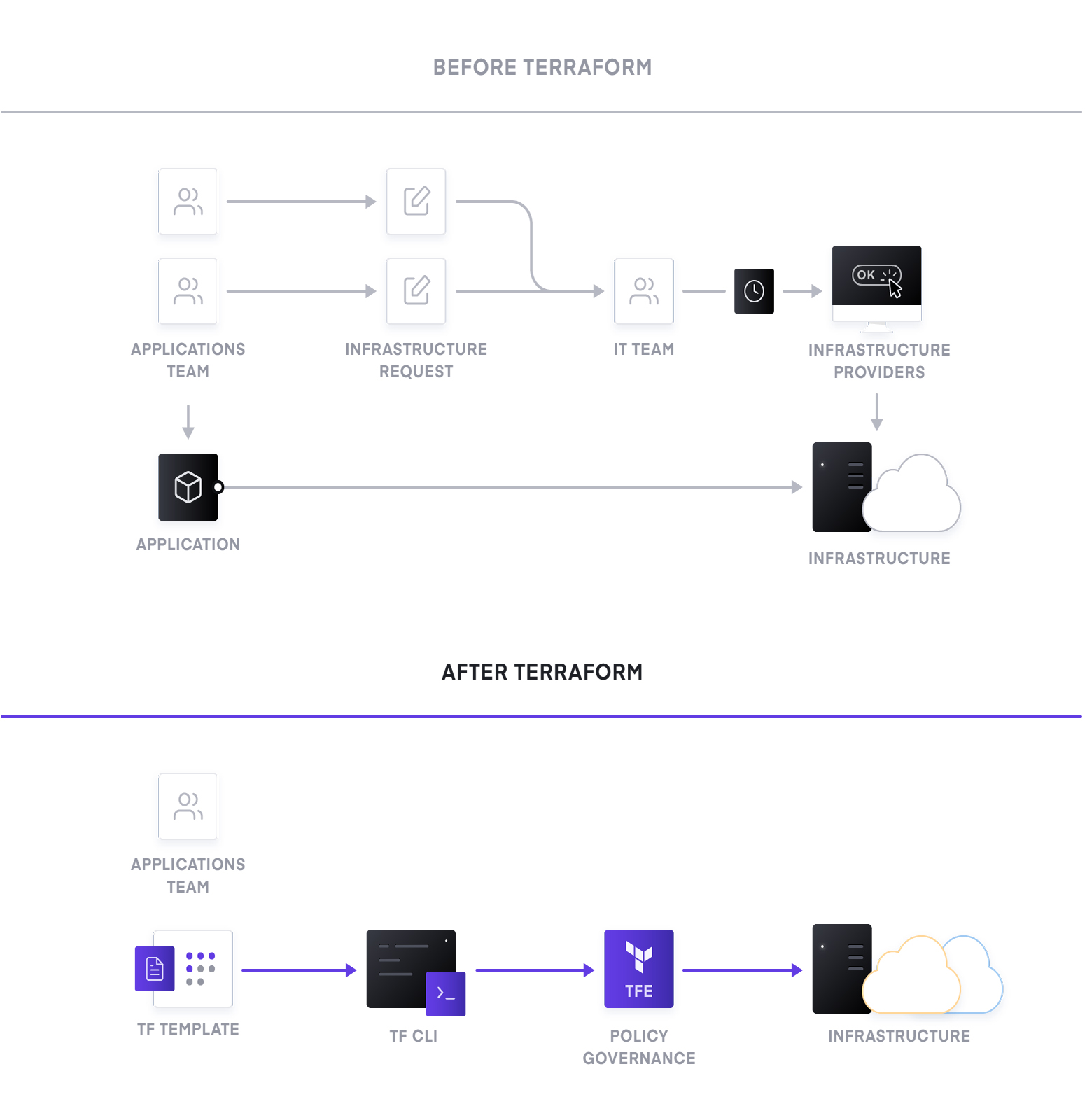
The first key challenges organizations must address is how infrastructure will be provisioned and managed. In today‘s on-premise environments, infrastructure is manually setup which relies on a ticketing and queuing system that can often attract lengthy delays. Using this workflow, no quality control exists, and it is not possible to reproduce infrastructure configuration to enable debugging or testing before rolling out configurations to production.
The adoption of Infrastructure as Code in the organization is essential to address this challenge. Infrastructure as Code is the practice of using code to describe infrastructure and services along with their respective configurations, which is both human readable and machine consumable. Our recommended tool for this problem is HashiCorp Terraform. You describe the infrastructure and configuration that you want and Terraform will determine the order of the steps that need to be applied. The desired state is expressed in a simple human readable language, after which Terraform can determine the sequence in which the infrastructure needs to be created.
We love Terraform for its simplicity and how easy it is to learn and use, in addition to the fact that Terraform supports over 200 providers including hardware, PaaS, IaaS and SaaS services. This means that Terraform can provision to more than just the cloud. It can provision and configure on-premise tools like VMWare, Venafi and InfoBlox as well as network security appliances like F5, FortiOS, Cisco, Palo Alto and Check Point devices. This extensible provider support allows complex infrastructure to be setup from a single Terraform run.
Incorporating Infrastructure as Code into the development lifecycle means that tried and tested software engineering processes can be adopted. This includes managing source code in version control and using branching strategies to allow for localized testing before pushing configuration to a production environment. Using pull requests before merging code can allow teams to review changes before they are committed to upstream branches. The configuration of infrastructure is also reproducible and allows a dev environment to be replicated into production.
With infrastructure configuration codified, it can be managed using well-known and well-tested software engineering practices such as version control, branching, pull requests and CI/CD tooling. Code can be reviewed by the necessary teams before it is committed to upstream branches. An example of this would be that a developer needs to adjust a permissions policy. The developer can make the change and commit it into source control after which the developer can then create a pull-request to merge the new permissions into the policy. A predefined set of people can then review and approve the change or ask the developer to make revisions as appropriate.
Building Security into the development lifecycle
Working in the financial services industry for over 20 years, we know that security is one of the top concerns our clients have during the cloud journey. There are many stories of data getting exposed from misconfigured S3 buckets, Elastic Search instances, databases and SIEMs to name a few. Developers should not need to be AWS S3 experts to use the service in a secure manner that complies with the organization’s security and compliance standards.
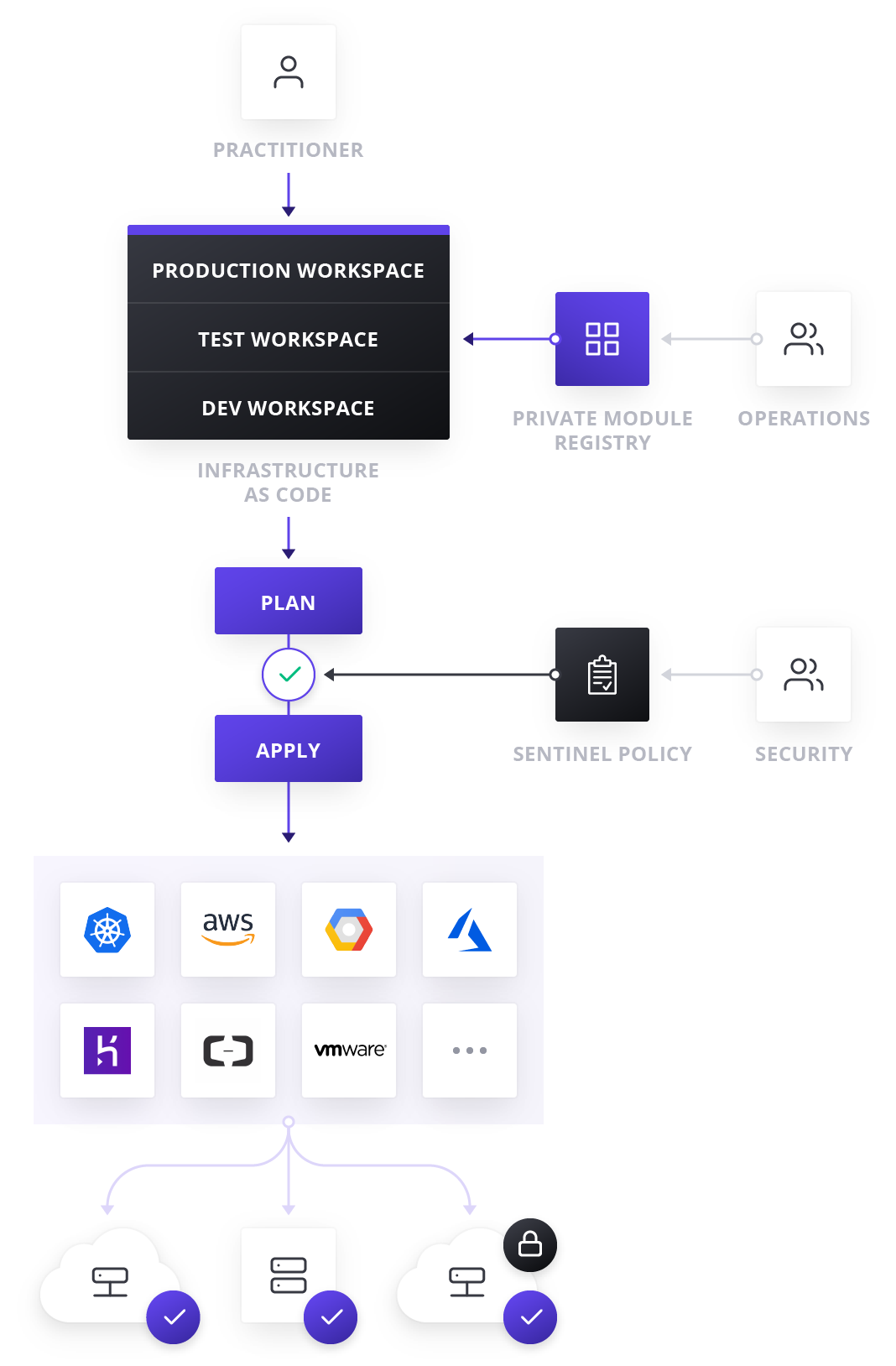
To solve this challenge, Terraform has the capability to consume modules. Modules are reusable and adaptable building blocks for cloud infrastructure and services. They are a set of predefined and prebuilt terraform code which describe common architecture and patterns that the organization uses. Modules are created by experts in the organization in consultation with security teams so that they adhere to policies, frameworks, and standards of the organization.
Once these modules have been created, they can be uploaded to source control and module registries where they can be consumed by the organization. By using the modules, developers and IT professionals know that the infrastructure they are spinning up adheres to company policy even if they are not experts in the infrastructure that they are creating. This enables developers to focus on solving business problems rather than focusing on undifferentiated heavy lifting of setting up infrastructure.
Security teams can enforce policies on the type of infrastructure that can be created, how it is used, and which teams get to use it. HashiCorp’s Sentinel Policy as Code Framework, can also be used to provide compliance and governance without requiring a shift in the overall team workflow and is defined as code too, enabling collaboration and comprehension for DevSecOps teams.
By adopting this way of working, organizations allow developers to build infrastructure that complies with policies and moves away from ticket-based systems for infrastructure to be created. These systems can often result in developers waiting weeks or longer to provision infrastructure.
Terraform Cloud & Terraform Enterprise
Terraform comes in three flavors: open source, cloud, and enterprise. Terraform open source is distributed as a single binary and is available using a CLI. When working in a significant team, state management and resource runs may become an issue. Terraform Cloud solves this problem and is the fastest way to adopt Terraform. Terraform Cloud is offered as a service where practitioners, teams, and global businesses can collaborate on infrastructure and manage risks for security, compliance, and operational constraints. Terraform Enterprise is deployed on infrastructure in your environment and can facilitate collaboration, governance, and self-service workflows on top of the Infrastructure as Code provisioning from open source.
Both Terraform and Enterprise provide workspaces, modules, and other powerful constructs for teams working together to build infrastructure. Modules can be uploaded to registries which will enable developers to quickly provision infrastructure in a self-service fashion. In addition, both platforms support SSO via an identity provider, logging and monitoring and dedicated support from HashiCorp. Both platforms also support Sentinel which is an embeddable policy as code framework to enable fine-grained, logic-based policy decisions that can be used by teams to limit certain actions, configurations or deployments.
Webinar – Unlocking the cloud operating model
Join Synthesis and Hashicorp for a webinar on where our experts deep dive into enabling operational excellence in the cloud using Terraform and Vault.
Time: 15:00
Date: Wednesday, 11 November